Certified Secure: SOC 2, ISO 27001, and Cyber Essentials—your assurance that we meet the highest industry standards.

With ISO 27001 certification, we maintain a comprehensive Information Security Management System (ISMS) that’s independently audited and continuously improved. From risk assessment to policy enforcement, every process is designed to safeguard your data and minimize vulnerabilities across our platform.

Cyber Essentials certification demonstrates that we proactively defend against the most common online threats. Through secure configuration, boundary firewalls, access controls, and regular monitoring, we protect your data and systems, helping your organization reduce exposure to cyber attacks.
MyContentScout runs on Amazon Web Services, leveraging its secure, scalable, and highly reliable infrastructure. This ensures your data is protected with advanced security controls, geo-redundancy, and automatic backups, so your team can access content anytime, anywhere with confidence.

With strong encryption, clear access controls, reliable cloud architecture, and built-in compliance, MyContentScout keeps your data safe, private, and always in your hands.
Your data always stays in your control. Each customer’s information is kept strictly separate, whether in our multi-tenant environment or through fully isolated deployments for organisations with stricter requirements. All data is encrypted both at rest and in transit, ensuring confidentiality and integrity from the moment it enters the platform to the moment it’s retrieved.
Access to information is tightly controlled so that users only see the data and documents they are authorised to. Ever-expanding integrations with tools like SharePoint and OneDrive, enable permissions which will seamlessly reflect your organisation’s existing rules. Single Sign-On (SSO) and Multi-Factor Authentication (MFA) are also on the way, giving enterprises even stronger control over authentication and user flows.
The platform is designed for availability and reliability, with a cloud architecture that spreads workloads across multiple zones. This approach minimises downtime and ensures your data and AI tools remain accessible, even if part of the underlying infrastructure experiences issues.
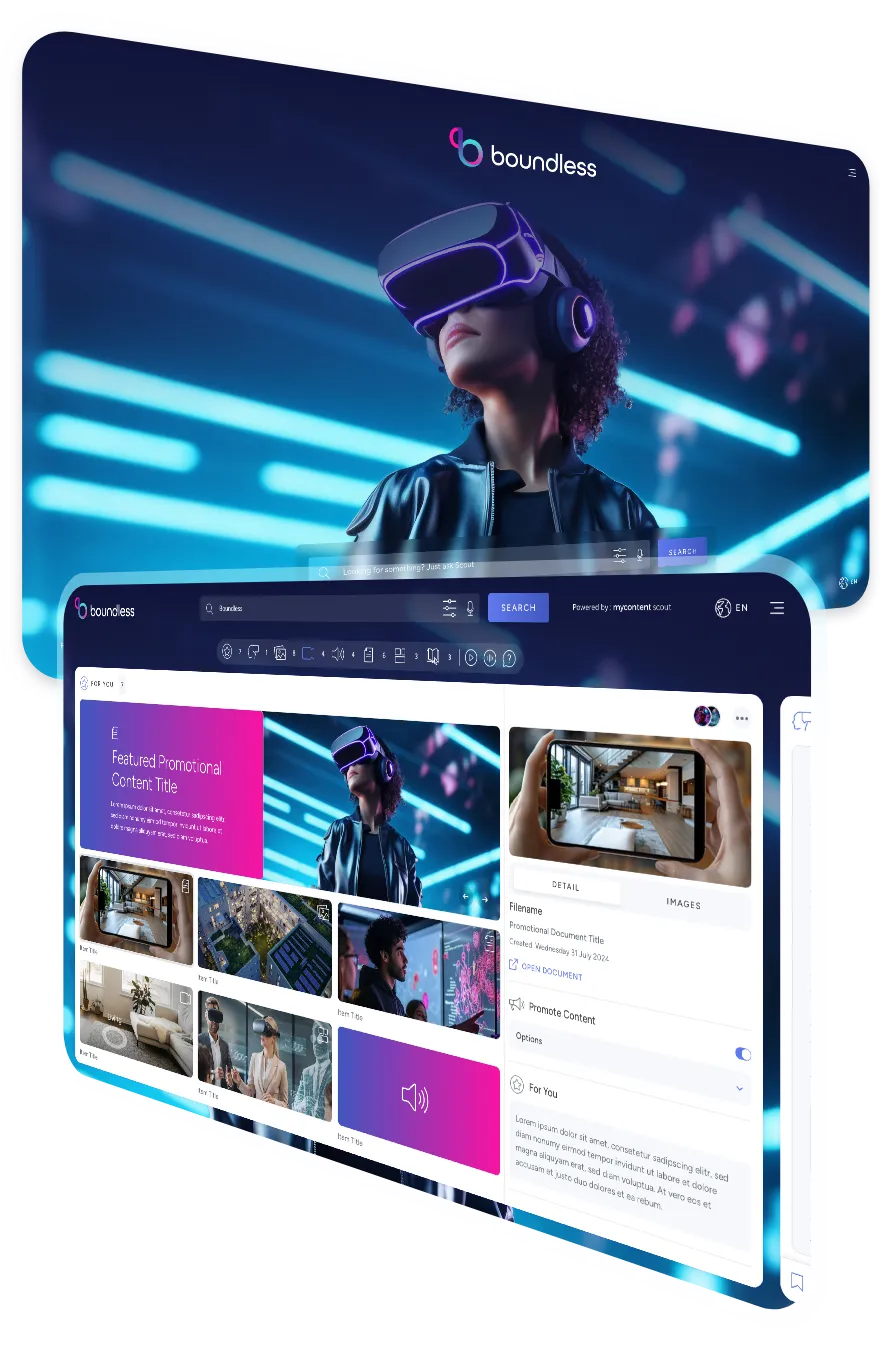
Our system doesn’t rely on generative AI. Instead, it delivers accurate summaries and search results directly from your company’s own documents and data, always linking back to the original source. That means no fabricated answers, no reliance on public data, and no risk of “hallucinations” - just reliable knowledge from within your own organisation. Your knowledge at your fingertips.
Built to be cloud-native, the platform integrates with native security features for auditing, monitoring, threat detection, and perimeter security. Security is continuous and proactive, with protections working in the background so your teams can focus on using the insights, not worrying about the infrastructure.
Security and compliance aren’t add-ons or tickboxes, they’re built in. The platform is designed to ISO 27001 and Cyber Essentials standards, with practices aligned to GDPR for lawful and transparent data handling. Our commitment to compliance doesn’t end there, as we are also progressing towards SOC 2, underlining our commitment to continuous improvement and meeting the highest standards of enterprise security.

Get in touch with our team to arrange a demo of MyContentScout and see how it could transform your workflow with AI search, content analysis and categorisation, saving you time and providing smart insights from various sources.